STORING AND SAFEGUARDING CLASSIFIED MATERIAL
(CT:DS-427; 07-16-2024)
(Office of Origin: DS/SI/IS)
12 FAM 531 GENERAL
(CT:DS-396; 01-27-2023)
(Uniform State, OPIC, USTDA)
a. Store classified material only in a manner that conforms to the provisions of this subchapter.
b. Whenever classified material is not under the personal control and observation of an authorized person, store it in an approved locked container under the conditions cited in this subchapter. Domestically, for the Department, contact the Office of Information Security (DS/SI/IS) via DSAPD@state.gov regarding open storage.
c. Classified information stored, processed, or transmitted on a Department information system or on Department media must meet the requirements of 12 FAM 630, 12 FAH-10 and, additionally, 12 FAH-6 H-540 if overseas. For more information, contact the Directorate for Cyber and Technology Security (DS/CTS) via AskCTS@state.gov on OpenNet, or AskCTS@state.sgov.gov on ClassNet.
d. The Department has developed and approved revised security standards for the storage of classified material at facilities abroad. These standards were coordinated with the Overseas Security Policy Board (OSPB) (See 12 FAH-6) and apply to all personnel and facilities under chief of mission (COM) authority (see 12 FAM 531.1 and 12 FAM 531.2.)
e. At Foreign Service posts, separate guidelines protect material relating to intelligence sources and methods.
f. Do not store classified material at a facility outside the chancery, consulate, etc., merely for convenience. To store classified material at an off-site location, a post must demonstrate to the regional security officer (RSO) a legitimate need to have material at a given location, and obtain the express written authorization of the RSO.
g. Separately located Voice of America (VOA) stations must not store classified information. VOA staff must make arrangements to store and read classified information at posts with classified storage and processing. In accordance with 12 FAM 536.9-6, Department personnel with an appropriate security clearance may take classified material from the storage site to a VOA facility during working hours, but the employee must either return the material at close of business or destroy it with an approved device (see 12 FAM 539.6). Sensitive But Unclassified (SBU) material may be stored at VOA facilities.
h. 12 FAM 570 covers storage requirements for contractors cleared for access to Department classified information.
12 FAM 531.1 Authorities
(CT:DS-392; 11-07-2022)
Relevant legal authorities include, but may not be limited to:
(1) Omnibus Diplomatic Security and Antiterrorism Act of 1986, Public Law 99-399; 22 U.S.C. 4801, et seq. (1986), as amended;
(2) Executive Order 13526, Classified National Security Information, December 29, 2009;
(3) Information Security Oversight Office (ISOO) Implementing Directive, 32 CFR Parts 2001 and 2003, June 28, 2010.
12 FAM 531.2 Top Secret Storage
(CT:DS-427; 07-16-2024)
12 FAM 531.2-1 Domestic
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
Storage of Top Secret (TS) material is approved in either of the following:
(1) General Services Administration (GSA)-approved container with a GSA-approved, built-in, three-position, dial-type combination lock; locate this container either in a DS-approved alarmed area or in a building controlled by cleared U.S. citizen personnel on a 24-hour basis; or
(2) Domestic strongroom (see 12 FAM 013 definition) approved for TS storage by the Program Applications Division (DS/IS/APD).
12 FAM 531.2-2 At Foreign Service Posts
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
OSPB standards do not allow open storage of classified material in a vault, except material in sealed diplomatic pouches, unless specifically authorized in writing by the Countermeasures Directorate (DS/C). See 12 FAH-6 H-313, OSPB Security Standards and Policy Handbook or for additional storage standards abroad based on Security Environment Threat List (SETL) rating.
12 FAM 531.3 Secret and Confidential Storage
(CT:DS-427; 07-16-2024)
12 FAM 531.3-1 Domestic
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
Storage of Secret and Confidential material is approved:
(1) In the same manner authorized for Top Secret (TS) information (see 12 FAM 531.1);
(2) In a barlock cabinet equipped with a GSA-approved three-position, dial-type, changeable, combination padlock located either in a DS-approved alarmed area, or in a building controlled by cleared U.S. citizen personnel on a 24-hour basis; or
(3) In a domestic strongroom or vault approved for Secret (S) storage by the DS/IS/APD division chief.
12 FAM 531.3-2 Foreign Service Posts
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
The Department does not allow open storage of classified material in a vault, except material in sealed diplomatic pouches, unless specifically authorized in writing by DS/C, (see 12 FAH-6 H-313), OSPB Security Standards and Policy Handbook, or for additional storage standards abroad based on SETL rating.
12 FAM 532 LOCKS
(CT:DS-427; 07-16-2024)
12 FAM 532.1 Electronically and Manually Activated Locks
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
Only DS-approved locks satisfy protection requirements for classified national security information. Other electronically activated locks (for example, cipher and magnetic strip-card locks) or mechanical locks that may not afford the required degree of protection prescribed in 12 FAM 531.2 and 12 FAM 531.3 are not authorized for the safeguarding of classified information. The DS Technology Development Branch (DS/FSE/TDB) identifies DS-approved locks through coordination with the OSPB, GSA, and other U.S. Government groups responsible for certifying locking devices for certain applications. Refer to the DS/FSE/TDB Web site for information regarding the level of protection afforded by specific DS-approved locks.
12 FAM 532.2 Changing Combinations
(CT:DS-427; 07-16-2024)
12 FAM 532.2-1 Individuals Authorized To Change Combinations
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Only individuals having an appropriate security clearance may change combinations to security containers and vaults protecting classified information:
(1) Domestically, individuals approved by the appropriate foreign affairs agency security office (see 12 FAM 511.1) may perform the combination change; and
(2) Abroad, RSOs, security engineering officers (SEO), security technical specialists (STS), Naval Support Unit Seabees, and information management officers (IMO) (for combinations within the Post Communications Center [PCC]) may perform combination changes.
12 FAM 532.2-2 When To Change Combinations
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
Change combinations under each of the following circumstances:
(1) When the lock is initially put into use;
(2) When a person knowing the combination no longer requires access to it, unless other sufficient controls exist to prevent access to the lock;
(3) Upon knowledge or suspicion that an unauthorized person knows the combination;
(4) When a security violation results from an unsecured security container;
(5) At least once every six months when the lock is used to control access to a computer room or an area for secure communication (all locations, both domestic and abroad), and at least once every 12 months when the lock is used for domestic strongroom doors, for domestic open storage area doors, or at locations abroad for daytime or nighttime access control to containers or spaces where classified information is stored, processed, or discussed; or
(6) When moving GSA-approved containers with combination locks from active to inactive status, reset domestic containers to the factory combination (50-25-50). Abroad, reset containers to the post security combination provided by the RSO. Set all S&G 8077 combination padlocks removed from service to a combination of 10-20-30 and retain them in a secure space. See 12 FAM 539.2 paragraph(g) for additional information on clearing containers removed from active use.
12 FAM 532.2-3 Recording Combination Changes
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. Record all combinations to classified containers and repositories on Form SF-700, Security Container Information. Classify records of combinations (containers, built-in combination locks, vault doors, padlocks, MDLs, etc.) at the highest level of classified material stored in the security container.
b. At Foreign Service posts:
(1) Complete form SF-700 in its entirety and file the form in the central repository normally used in the custody of post security officers (PSOs) or RSOs; or
(2) In the case of Core combinations, store within the PCC according to distribution instructions printed on the SF-700.
c. Domestically, the activity's assigned unit security officer (USO) will store Form SF-700.
12 FAM 532.2-4 Storage of Combinations
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. Store combinations only in repositories authorized for the storage of material at the highest classification level to which combinations permit access. Combinations may not be recorded in hardcopy except on Form SF-700 or on combination lists that are posted inside repositories for shared containers in the immediate area. Combinations must be committed to memory.
b. Do not store combinations electronically in a computer file or on the network because this does not provide sufficient need-to-know access restrictions. Alternatively, combinations may be stored on a Department-owned and IT Configuration Control Board (IT CCB) approved encrypted thumb drive. Media must be marked indicating the highest classification of information and protected in an approved security container.
c. Combinations to repositories containing official funds are subject to the requirements of 4 FAH-2 H-230 and the instructions from the responsible RSO or PSO abroad. Do not store money or other high-value items in a security container with classified information.
d. Use Form SF-700 to post the names of personnel having knowledge of the combination on the inside of the control drawer for a GSA-approved safe file cabinet, on the protected side of a vault door, or on the inside of the top drawer for a barlock cabinet.
12 FAM 533 REMOVING CLASSIFIED MATERIAL FROM OFFICIAL PREMISES
(CT:DS-427; 07-16-2024)
12 FAM 533.1 Overnight Custody
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
Classified material may not be removed from official premises for reasons of personal convenience or kept overnight in personal custody. Classified material may not be removed from official premises except when necessary to conduct official meetings, conferences, or consultations. See 12 FAM 536.9-4 for requirements for hand-carrying classified material. Classified material must be returned to a U.S. Government facility or activity, or an appropriately cleared domestic contractor facility for storage immediately upon the conclusion of the meeting, conference, or consultation. Classified material must not be taken to a home or hotel for unattended storage prior to or following a meeting. See 12 FAM 531 for offsite storage overseas.
12 FAM 533.2 Certification Upon Permanent Departure from Post
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
When departing a post upon transfer, resignation, or retirement, each employee, irrespective of rank, must certify as part of the post clearance procedure that:
(1) They are not taking classified material from the post through any other than authorized means;
(2) Classified material is not in their household or personal effects; and
(3) Classified material will not be mailed or otherwise transmitted in violation of 12 FAM 536.9.
12 FAM 534 SAFEGUARDING CLASSIFIED MATERIAL
(CT:DS-427; 07-16-2024)
12 FAM 534.1 General Procedures
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
a. Employees using classified material are responsible for its custody and must take every precaution to prevent unauthorized access.
b. Employees must not leave classified material in unoccupied rooms or cubicles, or inadequately protected in an occupied office, or in an office occupied by individuals without security clearances and the need to know.
c. Photography, video, and all other unclassified visual recordings, video calls and video teleconferences are not permitted in Department areas where classified information may be processed, viewed, stored or discussed, except for the following:
(1) Collaborative computer devices (i.e., webcams and headsets) that support VoIP conferencing solutions (e.g. MS Teams, WebEx, Zoom, etc) and have been approved by the Department's Information Technology Change Control Board (ITCCB) may be used in domestic controlled access areas (DCAAs) only when no classified discussions are taking place in the immediate area and no classified information is in view of the device. DS recommends, and will provide upon request, positive disconnect devices that can be installed with the collaborative devices to enhance security.
(2) Department-issued mobile devices that have been ITCCB-approved for use in DCAAs may be used only when no classified discussions are taking place in the room or nearby and no classified information is in view. Additional controls must be employed, such as the proper placement of devices, use of virtual backgrounds and lens coverings, and compliance with TEMPEST separation requirements. Classified information must not be within the camera's field of view. All mobile devices must be powered off or removed from the office when any classified discussions take place.
(3) Department-issued, dedicated unclassified video teleconference (VTC) equipment that has been ITCCB-approved for use in DCAAs may be used only when installed in a conference room or private office, when no classified discussion is taking place, and when no classified information is in view. Unclassified VTC within a DCAA must be powered off or physically disconnected when not in use.
d. Employees must handle foreign government information (FGI) in the following manner:
(1) Safeguard FGI provided pursuant to an existing treaty, agreement, bilateral exchange, or other obligation in accordance with the governing document. See 5 FAM 482.6 and 11 FAM 520.
(2) Safeguard North Atlantic Treaty Organization (NATO) classified information in compliance with U.S. Security Authority for NATO (USSAN) Instruction 1-07;
(3) Provide a degree of protection for FGI at least equivalent to that required by the foreign government or the international organization that provided the information;
(4) Documents may retain their original foreign classification markings provided that they are adequate to meet the purposes served by U.S. classification markings. If there are no adequate foreign markings, mark the information with U.S. classification markings and protect accordingly. If there is any doubt as to the proper classification level of an FGI document, contact the Bureau of Administration's Office of Information Programs and Services (A/GIS/IPS) for guidance.
(5) The unauthorized disclosure of foreign government information is presumed to cause damage to the national security. See E.O. 13526 section. 1.1(d). Unless some factor overcomes that presumption, foreign government information that is provided in confidence and is not classified by the foreign government at a level the U.S. Government recognizes as equivalent to U.S. Confidential, Secret or Top Secret needs to be classified as U.S. Confidential within a reasonable period of time after receipt to protect it from unauthorized disclosure. For example, foreign government information marked “restricted” or “designated” may require such treatment.
(6) The information described in the above paragraph (12 FAM 534.1d(5)) may be handled under standards that are less restrictive than the safeguarding standards that ordinarily apply to U.S. Confidential information when adequate to achieve a degree of protection at least equivalent to that required by the providing government (See 5 FAM 482.6). The notation, ‘‘Modified Handling Authorized,’’ or “FGI/MOD” should be added to either the foreign or U.S. markings. Individuals being given access to the information must be notified of applicable modified handling instructions via briefing, written instructions, or a cover sheet (See 12 FAM Exhibit 534.1). In accordance with 5 FAM 731, classified information must be transmitted in a method approved for classified information, unless this method is waived by the originating government. Foreign government transmission of the information via an unclassified system is presumed to waive the requirement, in the absence of other indications of the foreign government’s expectations. When using the internet to transmit modified handling material to other U.S. Government agencies or other entities, the information should be safeguarded using Department-approved encryption methods when practical and available. Be aware that other U.S. Government agencies may have different policies on the transmission and handling of C//FGI/MOD information. Direct questions related to the protection of information authorized for modified handling to the DS_IS_Policy@state.gov mailbox on OpenNet; and
(7) To the extent practical, FGI should be stored separately from other information to facilitate its control. To avoid additional costs, separate storage may be accomplished by methods such as using separate drawers in the same container as other information or, for small volumes, the use of separate file folders in the same drawer. Electronic file separation on Automated Information Systems (AIS) can be accomplished with dedicated share drives. (Posts should consult with their bureau’s information systems security officer (ISSO) for detailed instructions or assistance.)
12 FAM 534.2 Closing Hours Security Check
(CT:DS-427; 07-16-2024)
12 FAM 534.2-1 Form SF-701, Activity Security Checklist
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Supervisors must institute a system of security checks prior to those conducted by security guards at the close of each working day, or as soon thereafter as administrative operations permit. Such a system determines that:
(1) All classified material, to include that processed on any automated information system, has been properly stored and that containers are locked;
(2) Windows and doors, where appropriate, are locked; and
(3) The area is otherwise secure and not susceptible to overt penetration.
b. To fulfill this mandatory requirement in all areas and at all echelons, supervisory officials must designate employees on a weekly basis to conduct a closing hour's security inspection of offices within a specifically defined area of responsibility. Such designees will use Form SF-701, Activity Security Checklist, to record the results of the closing hours security check. This form will be forwarded to the BSO, USO or RSO/PSO at the end of the month. The BSO, USO and RSO/PSO will maintain the record for 30 days and then destroy it unless an incident has occurred that would warrant longer retention.
12 FAM 534.2-2 Reporting Infractions
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
A deviation of the regulations discovered by an employee designated to conduct the closing security check is not to be construed as a security incident in itself. It should not be reported on Form OF-117, Notice of a Security Incident, unless the RSO/PSO/BSO determines otherwise or the closing hour's security check is, in fact, the final inspection where U.S. citizen guards or Marine Security Guards (MSGs) are not on duty.
12 FAM 534.2-3 Responsibilities
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Employees designated to conduct closing hour's security checks will, at a minimum:
(1) Ensure that all repositories containing classified material are secured;
(2) Ensure that all classified computer hard drives are removed and secured;
(3) Ensure that all thin clients and zero clients are powered down;
(4) Check the tops of all desks, including “in” and “out” boxes, and repositories to ensure that all classified and controlled material has been put away; and
(5) Make a visual check of the remainder of the office.
b. This section imposes a direct and important security responsibility on employees conducting closing hour's checks. Although custodians of classified material are responsible for its safekeeping in the Department, the checker, under certain circumstances, may be jointly charged with the violation.
12 FAM 534.2-4 Exceptions to Requirements
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
Exceptions to the closing hours security check requirements, based upon physical or personnel considerations such as the unusual number of repositories located in a specific area, communications areas, alarmed rooms and areas with few assigned employees, must be requested in writing to DS/SI/IS or the RSO/PSO and will be decided on a case-by-case basis.
12 FAM 534.3 Conferences
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. In conducting conferences where classified information or material may be involved, the operations element calling or conducting the conference must observe every precaution to ensure that:
(1) In the interests of technical security, classified conferences are held only on official premises certified for classified discussion;
(2) Proper physical security measures are implemented to provide protection for such information or material equal to the measures required during normal operations; and
(3) Participants are entitled to access to such information.
b. The operations element calling or conducting the conference should give advance notice to (and coordinate with) the appropriate post or RSO/PSO or DS/SI whenever:
(1) Classified material is to be removed from its normal place of storage and transmitted or carried to the conference site; or
(2) Participants are not personally known to have an appropriate security clearance by the officer calling or conducting the classified meetings.
12 FAM 534.4 Domestic Secure Mobile Communications
(CT:DS-392; 11-07-2022)
a. Consistent with E.O. 13526 and 32 CFR 2001, when an individual has been provided with secure mobile communications capability in accordance with 12 FAM 565, they must adhere to preventive technical, physical, personnel, and administrative control measures to protect against loss and/or unauthorized disclosure of classified information. The user must acknowledge and consent to the terms of the User Agreement. Specifically, the agreement will include, but is not limited to, the following administrative control measures:
(1) The user must have an active security clearance at the Secret level or higher and must maintain this clearance as long as the device is assigned to them. If the clearance is revoked or suspended at any time, the user must immediately contact DS/IS/APD to coordinate return of the device;
(2) The device is only approved for data and communications up to the Secret level and at no time may the device be used for Top Secret (TS) or TS/Sensitive Compartmental Information (SCI) communications. The device is unclassified until it is provisioned (keyed);
(3) Any device that provides secure voice capability shall be treated as "listen only" (a term defined in the user agreement) any time the user is outside a space authorized for classified discussion;
(4) If the device utilizes a cryptographic ignition key (CIK) the user must remove the CIK from the encryptor and power off when the device is not in use. The user will maintain the CIK on their person or otherwise secure it separate from the device when not in use;
(5) Whenever possible, the user will ensure the room in which the device is located is locked when not occupied and there is no unescorted access to the device;
(6) The user will not connect this device to any other device of any kind, and will not insert any removable media;
(7) The user will not use mobile devices (e.g., tablets, smartphones, smartwatches) or other personal electronic devices which utilize wireless technology (e.g., Wi-FI, Bluetooth, NFC) in areas where the secure communications equipment is located. These devices must be powered off with any camera lense(s) covered when secure communications equipment are in use;
(8) The user will remove or disable any devices with recording capability from the room housing the secure communications equipment prior to using the equipment for classified operations;
(9) The user will minimize risk of compromise of classified information by maintaining an awareness of their surroundings and proximity to uncleared individuals and by ensuring that no uncleared individuals are able to hear or see any classified information on or through the device;
(10) The user will close blinds, windows, and doors to adjacent areas when the equipment is in use;
(11) The user must immediately report lost, stolen, or damaged equipment to the DS Computer Incident Response Team (CIRT) at CIRT@state.gov; and
(12) Secure mobile communications are not authorized overseas except what is covered under the Secretary’s Technical and Information Security Travel Policy (STISP) version 18.1 dated 12/10/2018.
12 FAM 535 ACCOUNTABILITY AND CONTROL
(CT:DS-427; 07-16-2024)
12 FAM 535.1 Control Procedures
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Top Secret information may not be stored, processed, or transmitted on any Department unclassified system (e.g., OpenNet) or any Department system approved only for up to Secret information (e.g., ClassNet). It may only be processed on (1) a Department system approved for the processing, storage and transmission of Top Secret information; or (2) on TEMPEST equipment approved for the processing, storage, and transmission of Top Secret information.
b. Special access program (SAP) material and communications security (COMSEC) material must be accounted for and controlled by the procedures governing those programs (See 12 FAM 660 regarding COMSEC.)
12 FAM 536 ACCESS AND DISSEMINATION
(CT:DS-427; 07-16-2024)
12 FAM 536.1 General Access Requirements
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
A person must only be given access to classified information when that person has received an appropriate security clearance and such access is necessary in connection with the performance of official duties. Access to classified information is granted in accordance with the criteria given in this section, and when the person executes the Form SF-312, Classified Information Nondisclosure Agreement.
12 FAM 536.1-1 Determination of National Security Eligibility
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
a. A person must only be given access to classified information when a favorable determination has been made as to the person’s national security eligibility and they are granted a security clearance. National Security Eligibility (eligibility for initial or continued access to classified information or initial or continued eligibility to hold a sensitive position) is predicated on the individual meeting the personnel security standards as described in 12 FAM 233.
b. The Office of Personnel Security and Suitability (DS/SI/PSS) keeps a record of all security clearances for Department employees and certain cleared contractors. For the remaining cleared contractor employees performing on Department contracts, security clearance information is maintained by DS/IS/IND. Special and specifically authorized clearances are required for access to information identified as "Restricted Data", "NATO", "COSMIC", cryptographic, intelligence and other information given special protection by law or regulation.
12 FAM 536.1-2 Determination of Need-to-Know
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
A person is not entitled to receive classified information solely by virtue of official position or by virtue of having been granted a security clearance. A person must also have a need for access to the particular classified information sought in connection with the performance of official U.S. Government duties or contractual obligations, or as otherwise specifically authorized by these regulations. The officers with responsibility for the classified information must make the determination of that need.
12 FAM 536.1-3 Determination of Storage Capability
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
A person is not entitled to receive classified material solely by virtue of having a security clearance and a need to know. They must also have approved classified material storage facilities. Not all foreign affairs agencies or contractor facilities, domestically or abroad, have storage capability for classified material. Employees must contact the appropriate foreign affairs agency security office to verify storage capability.
12 FAM 536.1-4 Determination of Security Briefing
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
A person is not entitled to receive classified information until after they have received a security briefing covering the provisions of these regulations and has executed a non-disclosure agreement (Form SF-312).
12 FAM 536.2 Access by Historical Researchers and Former Presidential Appointees
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
In accordance with 5 FAM 474.4, the need-to-know requirement for access to classified information may, under certain circumstances and in accordance with E.O. 13526, be waived for historical researchers, former Presidents, former Vice Presidents, and individuals who have occupied senior policy-making positions to which they were appointed or designated by the President or the Vice President (or their appointees or designees). Additionally, as agency records for a particular period are declassified, they are transferred to the National Archives. Historical researchers; therefore, will normally be referred to the National Archives for research in such declassified records.
12 FAM 536.2-1 Department of State Records
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
For the Department, former Presidential appointees may apply to A/GIS/IPS for access to those documents which they originated, reviewed, signed, or received while serving as Presidential appointees, provided that all of the following conditions are satisfied:
(1) The Office of Personnel Security and Suitability (DS/SI/PSS) makes the determination that granting access to the intended recipient is consistent with the interests of national security and that the intended recipient is trustworthy. Access will be limited to categories of information over which the agency has classification jurisdiction;
(2) The intended recipient agrees in writing to safeguard the information from unauthorized disclosure in a manner consistent with applicable statutes and regulations;
(3) The intended recipient agrees in writing to authorize the review of notes and manuscripts for the purpose of determining that no classified information is contained therein;
(4) The intended recipient agrees in writing that the information involved will not be further disseminated without the express permission of the agency;
(5) The information requested is reasonably accessible and can be located and compiled with a reasonable amount of effort. Otherwise, A/GIS/IPS will charge fees to assemble the information, in accordance with the schedule in 22 CFR 171.6;
(6) Any individual or research assistant requiring access on behalf of the intended recipient must also meet all the above conditions. Such personal assistants must be authorized to be working for the former appointee exclusively and not gathering information for publication on their own;
(7) Information compiled by research assistants is similarly subject to all conditions enumerated above; and
(8) Upon request, such information as the recipient may identify will be reviewed for declassification in accordance with the provisions of these regulations.
12 FAM 536.2-2 Other Agencies’ Records
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. For the U.S. Trade and Development Agency (USTDA), former Presidential appointees and historical researchers may apply to the Bureau of Public Affairs (PA).
b. For the Overseas Private Investment Corporation (OPIC), former Presidential appointees and historical researchers may apply to the director of the Bureau of Legislative Affairs (H).
12 FAM 536.3 Access by Other Persons In The Legislative and Judicial Branches
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Provision of classified information by the Department to individuals or entities of the Federal legislative or judicial branches will be determined on a case-by-case basis by the H Bureau (for provisions to Congress), DS/SI/IS, A/GIS/IPS and the Office of the Legal Adviser (L), as appropriate and in coordination with other concerned bureaus; and in OPIC by the Director of Public Affairs.
b. Persons authorized to disseminate classified information outside the executive branch shall ensure the protection of the information in a manner equivalent to that provided within the executive branch.
12 FAM 536.4 Access by Contractors or Consultants
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. By agreement, the Secretary of Defense is authorized to act on behalf of the Department in rendering industrial security services. The Industrial Security Division (DS/IS/IND) will verify those contractor firms and personnel having current clearances to participate in classified contracts or purchase orders. For additional information, refer to 12 FAM 230 and 12 FAM 570.
b. Department employees are personally responsible for ensuring that DS/IS/IND has authorized consultants and/or contractors to have access to classified information prior to release of any such information.
12 FAM 536.5 Access by Foreign National Employees
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Classified information must not be made available to, or left in the custody of, foreign national employees. Do not permit such employees to attend meetings where classified information is discussed.
b. Classified information must not be dictated to or typed by foreign national employees. This restriction must not be circumvented by the assignment of classification after such an employee has prepared a particular document. National security information must not be entered into an AIS to which foreign nationals have access. The limitation against retroactively classifying data also applies to any document prepared on an AIS used by foreign nationals.
12 FAM 536.6 Controlling Dissemination
(CT:DS-427; 07-16-2024)
12 FAM 536.6-1 Other Federal Agencies
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. Classified information that originated in another Federal agency may be communicated by the receiving agency to a third agency without the consent of the originating agency unless that agency has determined that prior authorization is required for dissemination. For these purposes, the Department, Overseas Private Investment Corporation (OPIC), and the U.S. Trade and Development Agency (USTDA) are to be considered separate agencies. A recipient agency must not disseminate classified information to a third agency when the originating agency has determined that prior authorization is required for such dissemination and has marked or indicated such requirement on the medium containing the classified information (e.g., Originator Controlled (ORCON) markings under 12 FAM 536.7-2). With respect to internal Department distribution caveats such as exclusive distribution (EXDIS), recipient agencies would also be expected to limit further dissemination (see 5 FAH-4 H-213.1). Drafters should therefore apply appropriate markings, e.g., ORCON, to information which they determine requires continued control before dissemination to another agency.
b. Classified information may be sent to other federal agencies only through established liaison or distribution channels.
12 FAM 536.6-2 Intelligence Information
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Disclosures or releases of classified national intelligence including Sensitive Compartmented Information (SCI) must be approved by the Bureau of Intelligence and Research (INR). If there is any confusion as to whether a piece of information constitutes national intelligence information, the employee should consult with the originator and/or INR. At overseas posts when timely consultation with INR is not feasible, disclosure may be approved by an authorized official of the agency originating the information.
12 FAM 536.6-3 Classified Military Information
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. The National Disclosure Policy Committee (NDPC) establishes the procedures governing the release of classified military information to foreign governments and international organizations.
b. Direct all requests for the release of such information to:
National Military Information Disclosure Policy Committee
(NDPC)
Director, Office of Regional Security and Arms Transfers
Bureau of Political-Military Affairs
U.S. Department of State
Washington, D.C. 20520
12 FAM 536.6-4 Crypto Marking
(CT:DS-427; 07-16-2024)
(Uniform State, OPIC, USTDA)
A designation or marking of “CRYPTO” applied to cryptographic material indicates that it requires special consideration with respect to access, storage, handling, and accounting. Contact the appropriate foreign affairs agency security office regarding these procedures. For the Department, contact the Bureau of Diplomatic Technology’s Cryptographic Systems Branch (DT/FO/ITI/SI/CSB).
12 FAM 536.6-5 Dissemination Ordered or Requested by a Court of Law or Other Official Body
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Any subpoena, demand, or request for classified information, or records from a court of law or other official body must be handled in accordance with agency regulations (22 CFR Part 172; State, 5 FAM 473).
b. Testimony involving classified information is subject to the procedures for responding to subpoenas and must not be given before a court or other official body without the approval required by those procedures. An employee called upon to give such testimony without prior authorization must state that to disclose the information desired is not authorized and that a written request for the specific information should be transmitted to the head of the agency concerned. Such testimony, when so approved, must be given only under such conditions as the authorizing officer may prescribe.
c. All reports, records, and files relative to the loyalty of employees or prospective employees (including reports of investigative agencies) must be maintained in confidence and must not be transmitted or disclosed, except as required in the efficient conduct of business, and then only in accordance with applicable regulations.
12 FAM 536.7 Use of the Handling Caveats – Originator Controlled (ORCON), Not for Release to Foreign Nationals (NOFORN), and Releasable to (REL TO)
(CT:DS-427; 07-16-2024)
12 FAM 536.7-1 General
(CT:DS-377; 02-24-2022)
a. Under E.O. 13526, unless the originating agency indicates on the material that prior approval is required, a receiving agency may further disseminate the information to another agency or U.S. entity, including cleared state, local, tribal, and certain private sector entities. Similarly, under certain circumstances, receiving agencies may disclose or release classified information to foreign governments and international organizations.
b. For detailed instructions governing the disclosure or release of classified information to a foreign government or an international organization, see 11 FAM 520.
c. Employees have a responsibility to control the distribution of sensitive information. Standardized classification and control markings are the primary means by which the Department protects its information. The proper application and use of these markings enables information sharing while ensuring that the information is properly safeguarded from inadvertent or unauthorized disclosure. Dissemination control markings identify the expansion of or limitation on the distribution of Department information. These markings are in addition to and separate from the levels of classification. Examples of the types of information that drafters and classifiers should consider marking with dissemination controls include:
(1) Reports of negotiations on sensitive issues;
(2) Information identifying confidential sources;
(3) Reports containing sensitive security or threat information;
(4) Reports of conversations with senior foreign government officials;
(5) Political reporting on the character and personality of foreign officials; and
(6) Other information whose sensitivity might not be apparent to a recipient unfamiliar with the subject matter.
d. DS/SI/IS the primary Department authority for safeguarding national security information and should be consulted with respect to handling and dissemination questions. The Department’s primary authority for classification and declassification matters is A/GIS/IPS and should be consulted concerning original or derivative classification decisions.
e. ORCON - The ORCON marking is placed on classified national security information to indicate that it may not be disseminated outside of the recipient Department without prior approval. Information bearing the ORCON marking may be disseminated within the recipient agency and its subordinate elements, including to cleared contractors located within Government facilities. However, dissemination beyond the recipient agency or to agencies other than the original recipients requires advance permission from the originator. The ORCON marking may be applied by all personnel, including contract personnel, who have classification authority and have completed PK 323 - Classified and Sensitive But Unclassified Information: Identifying and Marking, regardless of whether the classification decision is original (e.g., by an original classification authority [OCA]) or derivative in nature. ORCON is to be applied sparingly as its use impedes efficient information sharing. The decision to apply the ORCON marking shall be made on a case-by-case basis using a risk management approach; it may not be applied in a general or arbitrary manner.
f. ORCON-USGOV - The ORCON-USGOV marking is placed on classified national security information to indicate that it may be disseminated to other Federal agencies but may not be disseminated outside of the executive branch without the prior approval of the originating agency. The ORCON-USGOV marking may be applied by all personnel, including contract personnel, who have original or derivative classification authority and have completed PK 323 - Classified and Sensitive But Unclassified Information: Identifying and Marking.
g. NOFORN - The NOFORN marking is placed on classified national security information to indicate that it may not be disclosed or released in any form to foreign nationals, foreign governments, or international organizations of governments without prior approval. See 5 FAH-1 H-232.10, NOFORN is applied to classified information by Department personnel, including contract personnel, who have original or derivative classification authority, and have completed PK 323 - Classified and Sensitive But Unclassified Information: Identifying and Marking.
h. In limited circumstances, the NOFORN handling caveat is applied to SBU information.
i. REL TO - The REL TO marking is placed on classified national security information to indicate that the determination has already been made to permit the release of the information to the foreign government or international organization of governments listed. The REL TO marking may only be applied when approved by an OCA or by subordinate officials designated by the OCA to make release decisions for a specific program or ongoing information exchange (see 12 FAM Exhibit 536.7-1). If the originator of the information is not an OCA or designated to make release decisions for the information and is classifying the information derivatively in accordance with 5 FAM 482.3, they must seek the approval of an OCA or designated official to include the REL TO caveat. The REL TO marking has the effect of NOFORN for countries not named in the marking. Releasing the information to an additional government requires an additional release decision. The first country in a REL TO marking is always the USA. REL TO markings, when used, should be applied in accordance with the following format:
(1) REL TO USA, followed by the approved trigraph of each country and tetragraphs of international organizations of governments, if appropriate, each in alphabetical order, separated by commas. (Example: SECRET//REL TO USA, GBR, JPN, ISAF, NATO)
(2) See also 5 FAH-1 H-232.11.
12 FAM 536.7-2 Removing ORCON or NOFORN Caveats
(CT:DS-339; 10-27-2020)
a. This guidance does not apply to, or authorize the disclosure or release of, classified information or classified intelligence information originated by another federal department or agency. Disclosures or releases of classified information with handling caveats originated by other Federal agencies must be preceded by consultations with, and the approval of, the originating agency. All intended disclosures or releases of intelligence information must first be coordinated with, and approved by, the Bureau of Intelligence and Research (INR). At overseas posts when timely consultation with INR is not feasible, disclosure of intelligence information may be approved by an authorized official of the element originating the information.
b. The Department may find it necessary in some cases to disclose or release classified information marked NOFORN or ORCON. Steps guiding the removal authorization include the following:
(1) Information marked ORCON may only be authorized for disclosure or release to an entity outside the Department by an official who has OCA;
(2) Information marked NOFORN may only be disclosed or released to a foreign government or international organization of governments when specifically authorized by an official who has OCA;
(3) This official with OCA may be:
(a) The official who initially authorized the classification of the material, if that official is still serving in the same position;
(b) The successor to the official who originally authorized the handling caveat; or
(c) The supervisory official of either.
(4) The official with OCA may designate a subordinate official to make release decisions, including the removal of ORCON or NOFORN for a particular program or ongoing information exchange (see 12 FAM Exhibit 536.7-1)
(5) Disclosure or release of TS NOFORN information can only be authorized by persons who have been delegated OCAs for TS information;
(6) When classified information is released to a foreign government or international organization of governments, the disclosing official should make a record of the disclosure and keep it with a copy of the disclosed material. This practice protects the releaser by documenting compliance with Department policy and facilitates future cooperation by providing important insight into how, when, and why national security-related information was provided to a foreign partner. Additionally, when the information is released (a physical copy provided to the foreign partner), a signed receipt of the release is required (See Classified Material Receipt, Form DS-112, and Receipt Manifest, Form DS-794, for examples of possible receipt forms.) This receipt should be kept with the record of the disclosure.
c. Information authorized for disclosure or release must have all NOFORN or ORCON markings, including portion markings, deleted or crossed through with a straight line. If appropriate, REL TO markings may be inserted.
12 FAM 536.8 Personal Use and Conversations
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Classified information must not be used for personal interests of any employee and must not be entered in personal diaries or other non-official records.
b. Employees must not hold discussions of classified information in the presence or hearing of persons who are not authorized to have knowledge thereof.
c. Employees must not discuss classified information in conversations on non-secure telephones or office intercoms.
12 FAM 536.9 Transmitting Classified Information
(CT:DS-427; 07-16-2024)
12 FAM 536.9-1 General Restrictions
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Classified material may only be transmitted physically across international boundaries by diplomatic courier or specially authorized nonprofessional diplomatic couriers, unless an exception is provided in accordance with 12 FAM 536.10. Nonprofessional diplomatic couriers are given such material for international transporting only in emergencies, when the professional service will not cover the area into which the pouch must be carried, or the professional service is unable to deliver the pouch to the post within the time that official business must be conducted. In such isolated cases, the nonprofessional diplomatic courier must be in possession of a diplomatic passport and a courier letter, and the material must be enclosed in sealed diplomatic pouches until delivered to its official destination. (See 12 FAM 100.)
12 FAM 536.9-2 Top Secret
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Top Secret information must be transmitted by either:
(1) Top Secret-cleared messenger;
(2) Authorized courier:
(a) Department of State Courier Service;
(b) Department of Defense Courier Service;
(c) Department of State nonprofessional courier; or
(3) Information system authorized for TS or TS/SCI processing:
(a) Top Secret Messaging Service, where available; and
(b) The Joint Worldwide Intelligence Communications System (JWICS), Intelligence and Research Information Support System (INRISS), or Intelligence Resource Information System (IRIS).
12 FAM 536.9-3 Secret (S) and Confidential (C)
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
When appropriately double-wrapped, Secret and Confidential information may be transmitted via:
(1) One of the means approved for TS;
(2) U.S. Postal Service (USPS) registered mail within and between the 50 states and the District of Columbia, the Commonwealth of Puerto Rico, or a U.S. territory;
(3) USPS Express Mail: USPS Express Mail can be used only when it is the most effective means to accomplish a mission within security, time, cost, and accountability constraints. To ensure direct delivery to the addressee, the “Waiver of Signature” block on the mail label may not be executed under any circumstances. All classified express mail shipments must be processed through mail distribution centers or delivered directly to a USPS facility or representative. The use of external (side street) express mail collection boxes is prohibited;
(4) Approved commercial delivery companies for transmission of Secret and Confidential material. Personnel may use companies approved by GSA for domestic express delivery services under Multiple Award Schedule 48. The list of approved companies is available at the GSA web site.
(5) USPS facilities on U.S. military installations. Mail containing classified information (i.e., official mail) must not be sent to posts through military postal service (MPS) or diplomatic postal service (DPS) facilities (See 14 FAM 750 and 14 FAM 760 for this prohibition.)
12 FAM 536.9-4 Policy for Hand-Carrying Classified Documents - General
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Due to the security risk inherent in hand-carrying classified material, supervisors will authorize hand-carrying only when:
(1) The classified material is required at the destination;
(2) The classified material is not available at the destination; and
(3) Because of time or other constraints, the classified material cannot be transmitted by another authorized means.
b. The classified material must be double-wrapped in accordance with 14 FAH-4 H-321a and 14 FAH-4 H-322, and in the physical possession of the custodian at all times, unless properly stored at a U.S. Government facility or appropriately cleared contractor facility (i.e., continental United States only).
c. Classified material must not be brought home or to a hotel for storage prior to a trip.
d. Hand-carrying classified material on trips that involve overnight stopover is not permitted without advance arrangements for proper overnight storage at an approved U.S. Government facility or approved contractor facility.
e. Classified material may not be read, studied, displayed, or used in any manner on a public conveyance or in a public place.
f. Classified material is not to be stored in any detachable storage compartment such as an automobile luggage rack.
g. Whenever possible, return the classified material to the parent organization by one of the other approved methods of transmission.
h. For trips outside the continental United States, follow the requirements of 12 FAM 100 for diplomatic couriers and authorized nonprofessional diplomatic couriers.
12 FAM 536.9-5 Domestic
(CT:DS-412; 08-21-2023)
(Uniform State, OPIC, USTDA)
a. Upon meeting the requirements of 12 FAM 536.9-4, domestic employees and contractors may transport collaterally classified information (i.e., non-sensitive compartmented information) up to and including TS information between diplomatic facilities within the Washington metropolitan area without the need for any courier authorization letter.
b. In some cases, however, outside agencies may require Department employees and contractors to obtain a courier letter prior to removing classified information from their facility. If a host agency requires visitors transporting classified information to carry a courier authorization letter, contact DS/IS/APD at DSAPD@state.gov.
12 FAM 536.9-6 Abroad
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. In countries with posts with a critical HUMINT (Human Intelligence) or TECHINT (Technical Intelligence) threat rating, the approval to transport classified material outside a Chief of Mission (COM) facility will require the approval of both the RSO and the deputy chief of mission (DCM).
b. Removal and hand-carrying of classified information from a diplomatic facility abroad, within the same country, must be authorized in writing by the RSO/PSO. The authorization, at a minimum, must include an inventory of the contents of the double-wrapped package and nonprofessional courier orders. The RSO/PSO will retain a copy of the authorization.
c. When classified information is hand-carried between diplomatic facilities within the same country, the RSO must decide whether a two-person escort is prudent and necessary. The RSO may also implement additional security measures as deemed appropriate given local threat conditions. These additional measures may include, but are not limited to, use of a U.S. embassy/consulate motor pool vehicle with an U.S. embassy/consulate driver, regular delivery update(s) to RSO and an RSO security briefing.
12 FAM 536.10 Classified Operations Support to High-Level Delegations Abroad
(CT:DS-427; 07-16-2024)
12 FAM 536.10-1 Secretary of State Travel
(CT:DS-396; 01-27-2023)
(Uniform State, OPIC, USTDA)
a. The Secretary's Technical and Information Security Travel Policy governs classified operations to support the Secretary's travel party.
b. RSOs ensure the travel policy's mandates are adhered to.
12 FAM 536.10-2 Other High-Level Delegations
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. All U.S. Government executive branch employees and contractors, except for those under combatant command or on the staff of an international organization (i.e., those not assigned to the post or present in country with a country clearance), including those members of high-level delegations, are prohibited from discussing, storing, reading, or processing classified information overseas outside of controlled access areas in diplomatic facilities. These employees and contractors must follow the OSPB standards regarding classified information in 12 FAH-6.
b. Requests for an exception to these 12 FAH-6 standards will be addressed on a case-by-case basis by the OSPB chair or designee. Requests should be directed to the Countermeasures Directorate (DS/C) and the RSO at the visiting post(s).
c. Members of the Secretary of Defense’s travel party or a combatant commander’s travel party are not subject to 12 FAH-6, but instead must consult Department of Defense regulations on the safeguarding and processing of classified information.
12 FAM 536.11 Reproducing Classified Documents
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
a. The number of copies of documents containing classified information must be kept to the minimum required by operational necessity to decrease the risk of compromise and reduce storage costs. All classified material must be reproduced sparingly and any general or specific prohibition against reproduction must be strictly adhered. No classified document is to be reproduced if such reproduction is prohibited by the originator and the document is so annotated. However, these provisions do not apply to documents reproduced for the purpose of conducting a declassification review. All documents reproduced during a declassification review must be destroyed as soon as they are no longer needed.
b. Unless a notation on the document or its cover restricts reproduction, permission is authorized without the approval of the originating department or agency for the reproduction of classified documents. Reproduction of the documents must be limited to that which is essential for efficient operations.
c. All agencies that reproduce paper copies of classified documents must maintain records to show the number and distribution of reproduced copies:
(1) Of all documents covered by special access programs distributed outside the originating agency;
(2) Those distributed within the agency if required by the special access program; and
(3) Of all Secret and all Confidential documents which are marked with special dissemination and reproduction limitations.
d. When a reproduction of a previously made copy is required, the copied document must show the authority for reproduction, the officer requesting reproduction, and the number of copies made.
e. Classified material should only be reproduced on approved reproduction machines that are under the continuous control of cleared U.S. personnel, in accordance with 5 FAM 1325.
12 FAM 537 DISPOSITION OR DESTRUCTION
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Classified material must be carefully and completely destroyed only through authorized means by appropriately cleared U.S. citizen employees (See 12 FAM 539.6.) See 12 FAM 630 for destruction requirements for classified media. (See 12 FAH-1, Emergency Planning Handbook, regarding emergency destruction of materials).
12 FAM 538 SPECIAL ACCESS PROGRAMS (SAP)
(CT:DS-427; 07-16-2024)
12 FAM 538.1 Policy
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
SAPs may be created or continued only under specific circumstances showing that:
(1) The vulnerability of, or threat to, specific information is exceptional; and
(2) The normal criteria for determining eligibility for access applicable to information classified at the same level are not deemed sufficient to protect the information from unauthorized disclosure.
12 FAM 538.2 Control and Administration
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Each office must appoint an official to act as a single point of contact for information concerning the establishment and security administration of all SAPs established by or existing in the office.
12 FAM 538.3 Codewords and Nicknames
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Excluding those programs specified in 12 FAM 539.7-1, paragraphs a and b, each SAP will be assigned a codeword, a nickname or both. Only the Assistant Secretary for Diplomatic Security (DS) through the official appointed under 12 FAM 539.7-2 must allocate codewords and nicknames for SAPs. All codewords and nicknames are unclassified.
12 FAM 538.4 Reporting Requirements
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Excluding those programs specified in 12 FAM 539.7-1, paragraphs a and b, offices administering SAPs provide annual reports (Report number F-92-1) to DS, submitting them not later than January 31 of each year, showing the changes in information provided under 12 FAM 539.7-1, as well as the date of last review. Annual reports must reflect actual rather than estimated numbers of carve-out contracts and persons granted access and must summarize the results of the inspections and audits required by 12 FAM 539.7-2, paragraph a. The information in the annual report must be as of December 31.
b. Administering offices must immediately notify DS/IS/APD upon termination of a SAP.
12 FAM 538.5 Limitations on Access
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Access to data reported under this section must be limited to the minimum number of properly indoctrinated staff necessary to perform the functions assigned to DS/IS/APD for the Department. Access may not be granted to any other person for any purpose without the approval of the office sponsoring the SAPs concerned.
12 FAM 538.6 “Carve-Out” Contracts
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. The official charged with the program and DS, or their designees, must ensure that, in those SAPs involving contractors, special access controls are made applicable by legally binding instruments (See 12 FAM 570).
b. Excluding those programs which are specified in 12 FAM 539.7-1, paragraphs a and b, the use of “carve-out” contracts that relieve the contractor from inspection responsibility under the Industrial Security Program is prohibited unless:
(1) Such contract supports a SAP approved and administered under 12 FAM 539.7-1;
(2) Mere knowledge of the existence of a contract or of its affiliation with the SAP is classified information; and
(3) DS/SI/APD approves “carve-out” status for each Department contract.
c. Approval to establish a “carve-out” contract must be requested from DS/SI/APD. Offices managing approved “carve-out” contracts must ensure the support necessary for the requisite protection of the classified information involved.
d. An annual inventory of “carve-out” contracts must be conducted by each office which participates in SAPs.
e. This section relates back to the date of execution for each contract to which “carve-out” contracting techniques are applied. The “carve-out” status of any contract expires upon termination of the SAP which it supports.
12 FAM 539 PROCEDURES FOR STORING AND SAFEGUARDING CLASSIFIED INFORMATION
(CT:DS-427; 07-16-2024)
12 FAM 539.1 Domestic Controlled Access Areas
(CT:DS-392; 11-07-2022)
(Uniform State, OPIC, USTDA)
a. Within domestic Department facilities, discussions, closed storage, and information system processing of collateral classified information may only take place within domestic controlled access areas (DCAAs). The only exception to this is the “listen only” provisions of 12 FAM 534.4.
b. When the Department builds or acquires domestic work space, DS conducts surveys to ensure the space meets requirements under Department policy for information system facility security and domestic physical security standards. If DS designates the space as meeting the standards for classified storage, discussion, and processing, it is then designated for that use by the space owner, the space is a DCAA.
c. Department space owners are required to contact DS/IS/APD to request a review and survey of their DCAA spaces. The purpose is to establish standards of use specific to that space, based on workflow requirements and environmental considerations. At the conclusion of the review, DS/IS/APD will provide to the space occupant and the occupant’s Executive Office a "DCAA Security Compliance Memorandum," which will specify the safeguards that must be in place to work within the DCAA (e.g., only employees with a minimum Secret clearance may work in the space). Occupants of the space are required to keep a copy of the DCAA Security Compliance Memorandum on file and must adhere to it.
d. Any occupant of a DCAA that does not have a current memorandum on file must contact their BSO or bureaus not assigned a BSO must contact the division chief of DS/IS/APD to request a review and memorandum.
e. Any time there is a change to the intended use of a DCAA space (e.g., employees wish to discuss, process, or store information at a different classification level), or a change to the physical configuration of the space, the occupant must contact DS/IS/APD to modify the DCAA Security Compliance Memorandum. For configuration changes, DS/IS/APD will coordinate with (DS/PSP/FSD).
f. DCAA occupants who do not adhere to the standards established in the DCAA Security Compliance Memo are at greater risk for a security incident, in accordance with 12 FAM 550, and may be subject to a Management Review Referral memorandum from DS/IS/APD.
12 FAM 539.2 Precautions
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. Holders must use open/closed signs on every repository containing classified material to indicate that the container is either open or locked. The cognizant foreign affairs agency security officer can provide information regarding procurement of these signs.
b. All personnel handling classified, and administratively controlled material are responsible for placing a cover sheet on the material to prevent unauthorized access and to alert personnel of the requirement for proper storage. Form SF-703, Top Secret Cover Sheet, Form SF-704, Secret Cover Sheet, and Form SF-705, Confidential Cover Sheet, are the only authorized cover sheets for classified information.
c. Holders must affix a Form SF-702, Security Container Check Sheet to every repository containing classified material and employees opening or closing the container must complete the appropriate column (Any person opening a container is responsible for securing it or obtaining explicit concurrence from another employee that they will secure it.)
d. Holders must affix a Form SF-701, Activity Security Checklist adjacent to at least the main exit door of every office where classified material is stored. This form is to be initialed at the end of the day by either the assigned security checker of the day or the last person to leave the office.
e. Personnel must ensure that classified repositories are locked and should check and initial those repositories that had not been opened since the previous check prior to leaving the room unattended. When securing a combination lock, turn the dial at least four complete turns in the same direction after closing. At the end of the day, the security checker is to check the lock and initial the Form SF-702, certifying that the lock has been secured by attempting to open the lock, drawers, or door. Anyone remaining after normal working hours is responsible for securing and checking their own safe.
f. Employees must immediately report defects or malfunctioning of storage equipment or locking devices to the USO or the RSO/PSO. Uncleared personnel are not permitted to service any equipment to be used for the storage of classified material.
g. Before taking security containers out of use, custodians must thoroughly inspect them to ensure all classified material has been removed and a standard combination set. The USO and the accountable property officer will also inspect the property, sign the Form DS-586, Turn-In Property Inspection Certification, and affix the completed form to the property. When checking safes that contain drawers, custodians must remove the drawers and completely inspect the inside of the safe. When containers are moved from inactive to active service, custodians must inspect the container and locks for possible tampering. See 12 FAM 561 and 14 FAH-1 H-722.
h. Classified material must not be stored in desks or anywhere other than in approved storage containers.
i. Classified material, including disposable material such as rough drafts, shorthand notes, disk drives, removable media from TEMPEST-approved systems, and voice recording materials must be safeguarded and locked in appropriate security repositories whenever unattended. Unclassified voice recording materials should be safeguarded and locked in appropriate security repositories at the close of business. This is a sound security practice and is advantageous to efficient administrative operations. For these same reasons, a ”clean desk” policy of securing all classified and unclassified documents is strongly encouraged.
j. All keys to doors kept locked after working hours must be turned in to a U.S. citizen guard and released only to authorized personnel. Where no U.S. citizen guard is assigned, DS/SI/IS or the RSO may authorize personal custody of keys. Keep such instances to an absolute minimum. Domestically, doors will be secured by means of a DS-approved lock. DS/SI/IS or the cognizant RSO must approve beforehand all new door lock installations. Desks, bookcases, and credenzas are not permitted to be locked either domestically or at post.
12 FAM 539.3 Top Secret Cover Sheets
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Top Secret documents must be covered by a Top Secret Cover Sheet.
12 FAM 539.4 Authorized Special Distribution Captions
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. NO DISTRIBUTION (NODIS) means no distribution to other than addressee without the approval of the Executive Secretariat (S/ES). This caption is used only on messages of the highest sensitivity between the President, the Secretary and COMs. Documents bearing this special distribution caption must be treated as NOFORN. In addition to the caption handling requirements, these documents must be given the physical protection prescribed by their classification.
b. EXCLUSIVE DISTRIBUTION (EXDIS) means distribution exclusively to officers with essential need-to-know. This caption is used only for highly sensitive traffic between the White House, the Secretary, the Under Secretaries and COMs. Documents bearing this special distribution caption must be treated at a minimum as NOFORN. In addition to the caption handling requirements, these documents must be given the physical protection prescribed by their classification.
c. STATE DISTRIBUTION only (STADIS) precludes initial distribution to other federal agencies and is used when disclosure of certain communications to other agencies would be prejudicial to the best interests of the Department. This caption may be used in conjunction with the caption “EXDIS.” Material captioned “STADIS” is to be controlled, handled and stored in accordance with the classification level of the information involved.
d. For details regarding caption messages, see 5 FAH-4 H-314.7.
12 FAM 539.5 Procedures for Access and Dissemination
(CT:DS-427; 07-16-2024)
12 FAM 539.5-1 Covers and Envelopes
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Classified information must only be disseminated to individuals, organizations, and facilities with the capability to receive and safeguard it.
b. For Department contractor facilities, verify the safeguarding capability through DS/IS/IND (See 12 FAM 536.1-3).
c. Comprehensive instructions for the preparation and transmission of classified information via Diplomatic Pouch and Mail, USPS and domestic couriers are in 14 FAH-4 H-320.
12 FAM 539.5-2 Receipts and Registration
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
a. Employees must use a Receipt Manifest, Form DS-794, or other receipt approved by foreign affairs agency security offices for TS and Secret material transmitted outside the organizational control of the sender. These receipts may be used for the transmission control of any other material at the discretion of the sender.
b. Employees must use Form DS-794, Receipt Manifest, or other approved receipt, to cover the transmission of more than one classified document between the sender and a single addressee. Such receipts are forwarded in duplicate, so that the addressee may acknowledge receipt of the material by signing and returning a copy to the transmitter, retaining the original for addressee’s records. The unit maintaining records of receipt must retain such receipts for two years.
c. Except as provided for the control of TS material, originating and receiving elements or employees are not required to maintain additional logs of transmission and receipt of classified material other than to note internal distribution, which may be recorded on the original of Form DS-794, or other approved means. Two years after the date of transmission or receipt of classified material, receipts covering the transaction may be destroyed.
d. Each piece (envelope, package, or other outer cover) of classified material going through the internal mail and messaging service, and diplomatic pouch must use a Form OF-120, Diplomatic Pouch Mail Registration or similar barcode-readable control number from point of origin to addressee/destination. The originator is responsible for affixing appropriate registry forms and indicating proper classification (see 12 FAM Exhibit 539.5-2 and 14 FAH-4 H-222.1, paragraph c).
12 FAM 539.6 Procedures for Destruction
(CT:DS-427; 07-16-2024)
12 FAM 539.6-1 Destruction of Secret and Confidential Material
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Records of destruction need not be made for TS, Secret or Confidential material unless recording is required by special regulation. When destruction receipts are required, employees must record destruction on Form JF-58, Register-Destruction of Classified Material, or other form or log approved by the cognizant foreign affairs agency security office or the RSO/PSO. Information subject to special regulations such as NATO, Restricted Data, etc., must be destroyed and destruction recorded in accordance with requirements of the applicable regulation.
12 FAM 539.6-2 Using Burn Bags
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
All classified material, to include working papers, handwritten notes, and other equipment to be destroyed must be placed in containers designated as burn bags, which are clearly and distinctly recognizable as burn bags. Burn bags awaiting destruction must be protected by safeguards commensurate with the classification designation of the material involved.
12 FAM 539.6-3 Laser Toner Cartridges
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
Laser toner cartridges removed from equipment such as laser printers, facsimile machines, and copiers may be treated, handled, stored, and disposed of as UNCLASSIFIED without additional countermeasures after completing a print cycle. When a cartridge is removed prior to completing a print cycle, handle as UNCLASSIFIED after manually rotating the drum one full turn.
12 FAM 539.6-4 Destruction Methods
(CT:DS-377; 02-24-2022)
(Uniform State, OPIC, USTDA)
Classified material is normally destroyed by burning, shredding, or except for microforms, by disintegration. DS/C/ST maintains a list of approved destruction equipment. Any other method must have the approval of the cognizant foreign affairs agency security office. Destruction of classified microforms can only be accomplished by burning or by chemical means (i.e., immersion in an approved chemical solution for a specified period of time), in accordance with Department instructions. COMSEC material must be destroyed in accordance with 5 FAH-6.
12 FAM 539.6-5 Destruction of Classified Storage Media
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
All storage media which has been used for processing classified information must be destroyed in accordance with 12 FAM 630 and 12 FAH-6 H-540. Contact at AskCTS@state.gov on OpenNet or AskCTS@state.sgov.gov on ClassNet with questions. For other foreign affairs agencies, their employees must contact the cognizant security office for further information.
12 FAM 539.7 Procedures for Special Access Programs
(CT:DS-427; 07-16-2024)
12 FAM 539.7-1 Establishing a SAP
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. Procedures for the establishment of SAPs involving NATO classified information are based on international treaty requirements.
b. SAPs for foreign intelligence information under the director of the Central Intelligence Agency (DCIA), or those of the National Telecommunications and Information Systems Security Committee, originate outside the foreign affairs agencies and are subject to the directives and regulations of the DCIA.
c. Excluding those programs specified in paragraphs a and b of this section, SAPs may be established within the foreign affairs agencies by submitting to the agency head a complete justification which is to include:
(1) The rationale for establishing the SAP, including the reason why normal management and safeguarding procedures for classified information are inadequate;
(2) The estimated number of persons to be granted special access in the responsible component, other components, other U.S. Government agencies, contractors, and the total of such personnel;
(3) A summary statement pertaining to the program security requirements, with particular emphasis upon those personnel security requirements governing access to program information;
(4) The relationship, if any, to other SAPs in the Department or other U.S. Government agencies;
(5) The estimated number and approximate dollar value, if known, of “carve-out” contracts (see 12 FAM 538.6) that will be or are required to support the program;
(6) The component official who is the point of contact (last name, first name, middle initial, their position or title, mailing address and telephone number);
(7) The proposed codeword and/or nickname (see 12 FAM 538.3) of the program; and
(8) The proposed date of program establishment.
12 FAM 539.7-2 Reviews of SAPs
(CT:DS-339; 10-27-2020)
(Uniform State, OPIC, USTDA)
a. DS/IS/APD must be provided and will maintain a listing of all SAPs within the Department. DS/SI/APD will compile and maintain the list for all DCIA SAPs in the Department and the United States Agency for International Development (USAID). Within USAID (except DCIA SAPs), the Executive Secretary will maintain this list.
b. DS/IS/APD must conduct oversight reviews, as required, to determine compliance with this procedure and the general safeguarding of classified information. For DCIA SAPs in the Department, the Special Security Operations Division (DS/IS/SSO) will be the primary security office for oversight reviews. As necessary, DS/IS/SSO and DS/IS/APD will coordinate for assistance/support.
c. Excluding those programs specified in 12 FAM 539.7-1, paragraphs a and b, the office administering each SAP must review the program annually. To accommodate such reviews, the responsible office must institute procedures to ensure the conduct of annual security inspections and regularly scheduled audits.
d. SAPs, excluding those specified in 12 FAM 539.7-1, paragraphs a and b, or those required by treaty or international agreement, must terminate automatically every five years unless re-established in accordance with the procedures contained in 12 FAM 539.7-1, paragraph c.
12 FAM Exhibit 536.7-1
Sample Designation Memorandum
(CT:DS-339; 10-27-2020)

12 FAM Exhibit 534.1
Modified Handling Coversheet Example
(CT:DS-339; 10-27-2020)

12 FAM Exhibit 539.5-2
Diplomatic Pouch Mail Registration or Similar Barcode-Readable Control Number
(CT:DS-377; 02-24-2022)
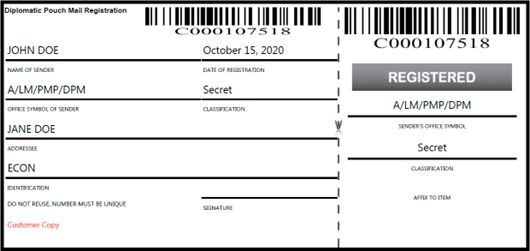
OF-120, Diplomatic Pouch Mail Registration (sample)
This form can be generated in the A/LM/PMP/DPM website

Sample of barcode-readable control number.